Keeping pace with today’s business landscape demands a hyper-efficient team. Optimizing team productivity isn’t therefore just nice to have: it’s a game-changer. But how do you jump-start your team’s efficiency? This guide has you covered, offering five tried-and-tested techniques that will propel your team toward peak performance.
Blog
Data Security Matters a great deal
A Mac user’s guide to malware warfare

The myth of Macs being invincible to malware has long been shattered. But there are those who still believe this myth, and so may find themselves facing the chilling reality of a Mac malware infection. For businesses, especially, the consequences can be disastrous: stolen data, compromised accounts, and operational disruptions that cost time and money.
Boost your efficiency in 2024 with these Android productivity apps

Today, Android users have countless apps to choose from to help them stay organized, focused, and efficient. But with so many options available, it can be overwhelming and time-consuming to find the right apps. To help you decide, here are seven essential productivity apps for Android that are sure to boost your efficiency in 2024.
1. Task Management: Todoist
Todoist is a versatile task management app that can help you organize your to-do lists and stay on top of your work.
Windows 11 made easy: 6 Features to boost your laptop’s security and performance
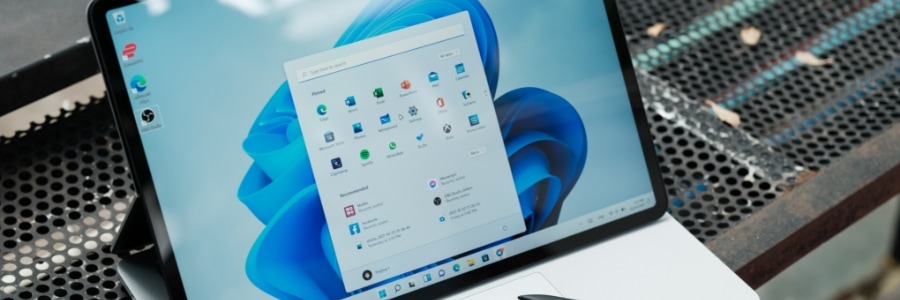
Microsoft’s latest operating system, Windows 11, brings numerous improvements compared to its predecessors. To get the most out of these improvements on your Windows 11 laptop, set up these six key features.
1. Software update settings
New laptops typically automatically check for updates, but it’s always a good idea to check manually every now and then to ensure you have the latest security patches and bug fixes.
A strategic guide to web hosting solutions

In today’s digitally driven landscape, a robust online presence is no longer a luxury, but a critical business imperative. Regardless of your industry or size, a website serves as the cornerstone of your digital infrastructure. However, constructing your online home requires a reliable foundation — namely, a web hosting service.






